After the yr 2000, when know-how use and improvement skyrocketed, the development of cyber threat has been cumulative.
The cybersecurity sector focused on new safety requirements and compliance throughout this time, after which went past compliance to have a look at the core enterprise dangers posed by cyber threats.
In 2022 and past, the trade and society have matured, and we’re now specializing in safety suites and infrastructure unification, in addition to managing cyber dangers. The alternatives and driving elements of 1 decade don’t take the place of these within the one earlier than it.
As a substitute, they broaden the attitude and emphasize well-known concepts in new methods. One such instance is DNS – though its roots will be traced again to 1966, DNS safety have to be part of each strong cybersecurity technique immediately.
What’s DNS safety?
Questioning what precisely DNS safety is and why it issues for your corporation? Allow us to first take a look at DNS and the way it began.
The Area Identify System (DNS) is an web protocol that gives human-readable names for a wide range of web-based providers, together with e-mail. Appearing because the phonebook of the web, DNS converts human-readable names to IP addresses, then modifications IP addresses again to names.
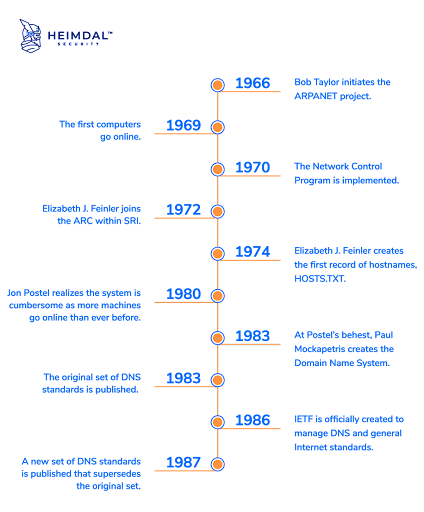
The mission began by American Web pioneer Bob Taylor in 1966 and referred to as Superior Analysis Tasks Company Community (ARPANET) represents the start of DNS historical past. Names to deal with translations had been previously saved on the ARPANET in a single desk contained inside a file referred to as HOSTS.TXT. This doc was used to manually assign addresses.
Nonetheless, sustaining the addresses manually had grown in depth and difficult. In consequence, American laptop scientist Paul Mockapetris proposed a brand new framework in 1983 that supplied a dynamic and distributed system referred to as the Area Identify System.
With the assistance of Mockapetris, the DNS grew to become in a position to lookup IP handle names moderately than simply hostnames, making it simpler for normal customers to entry the online. Merely put, with out it, there could be no web as we all know it immediately.
 Supply: Heimdal Safety
Supply: Heimdal Safety
Moreover, the Area Identify System Safety Extensions (DNSSEC) protects DNS from threats like cache poisoning and ensures the safety and confidentiality of information. All server responses are digitally signed by DNSSEC servers. DNSSEC resolvers verify a server’s signature to see if the knowledge it acquired matches the knowledge on the authoritative DNS server. The request is not going to be granted if this isn’t the case.
So what precisely is DNS safety?
DNS safety refers to all of the procedures created to maintain the DNS infrastructure secure from cyber threats with the intention to keep velocity and dependability, and forestall the (typically) disastrous results of cyberattacks.
Why is DNS safety vital?
DNS supplied us with the web as we all know it immediately. How a lot do you assume it might have developed if folks needed to keep in mind lengthy strings of numbers as a substitute of domains?
It is apparent that almost all of web customers use domains to explain the web sites they want to entry. Nonetheless, computer systems make use of IP addresses to tell apart between varied internet-connected programs and to route site visitors over the web. By enabling using domains, the Area Identify System serves because the web’s spine and makes it practical.
DNS as a safety vulnerability
Though its significance is unquestionable, DNS was not essentially designed with safety in thoughts. Subsequently, there are a lot of cyberattacks that may have an effect on it – cyberattacks that may influence firms’ cash, workflow, and popularity.
The most typical DNS dangers embody denial-of-service (DoS), distributed denial-of-service (DDoS), DNS hijacking, DNS spoofing, DNS tunneling, DNS amplification, DNS typosquating.
DNS safety dangers
DNS assaults are among the many most prevalent and efficient internet safety threats. Let’s focus on extra about them.
DNS assault sorts
Beneath are frequent DNS assault sorts.
- DoS: A denial-of-service (DoS) assault goals to convey down a pc system or community in order that its meant customers are unable to entry it. DoS assaults obtain this by sending the goal an extreme quantity of site visitors or data, inflicting it to crash.
Malicious actors that make use of DoS assaults steadily goal the online servers of well-known firms in industries like media, banking, and commerce, in addition to governmental and business organizations.
- DDoS: A distributed denial-of-service (DDoS) assault takes place when a number of programs coordinate a synchronized DoS assault towards a goal. Subsequently, the primary distinction from DoS is that the goal is attacked concurrently from a number of spots moderately than only one.DDoS assaults can have an effect on the shopper expertise and workflow, but additionally the income and model popularity.
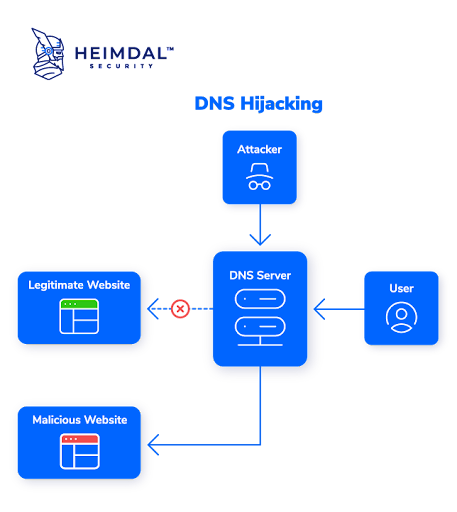
- DNS hijacking: Attackers use DNS hijacking, also called DNS redirection, to direct customers to malicious web sites by misresolving DNS requests. If malicious gamers management a DNS server and direct site visitors to a pretend DNS server, the pretend DNS server will then translate a sound IP handle into the IP handle of a malicious website.
 Supply: Heimdal Safety
Supply: Heimdal Safety
- Different oblique assaults: The crucial significance of DNS safety is underscored by the truth that different types of cyberattacks could use DNS as a instrument or be instruments utilized by hackers to compromise the DNS. Man-in-the-middle assaults, together with bot and zero-day assaults, are probably the most essential to say on this context.
DNS assault strategies
These are the commonest DNS assault strategies.
- DNS spoofing: DNS spoofing is an assault technique the place customers are despatched to a pretend web site that has been made to seem like an actual one, with the intention to redirect site visitors or steal consumer credentials.
Spoofing assaults can final for a really very long time with out being found and, as you possibly can think about, result in important safety points.
- DNS tunneling: Community site visitors is routed by means of the Area Identify System (DNS) utilizing a course of referred to as DNS tunneling to create an extra path for the transmission of information. Bypassing community filters and firewalls is simply one of many many makes use of for this method.
DNS tunneling will be employed maliciously to ship knowledge by means of DNS requests. This system is often used to spoof content material with out being observed by filtering or firewalls or to generate occluded channels for transferring data over a community that might usually not authorize the site visitors.
- DNS amplification: In DNS amplification assaults, the menace actor takes benefit of flaws in DNS servers to rework initially small requests into larger payloads which can be then used to overhaul the sufferer’s servers.
Usually, DNS amplification entails tampering with publicly accessible area identify programs by flooding a goal with a large number of Person Datagram Protocol (UDP) packets. The dimensions of those UDP packets will be magnified by the attackers utilizing a wide range of amplification methods, making the assault efficient sufficient to topple even the strongest Web infrastructure.
- DNS typosquating: Typosquatting is the fraudulent strategy of registering domains which have a robust resemblance to well-known manufacturers and corporations with the intention to deceive customers. The customers might enter the web site handle incorrectly and find yourself on a malicious website that completely resembles a respectable web site. The dangerous half is that customers would possibly then perform transactions and reveal non-public data.
Typosquatting is likely to be mixed with phishing and different on-line assaults.
How to make sure DNS safety
As will be seen within the IDC 2022 World DNS Menace Report, though the DNS assault influence on in-house utility downtime and cloud service downtime barely decreased in 2022 in comparison with 2021, the share of lack of enterprise and model harm elevated.
Customers want DNS with the intention to entry their apps and providers, whether or not they’re hosted regionally or within the cloud. If DNS providers are compromised, customers can’t entry their functions.
No DNS merely equals no enterprise, so whatever the measurement of the group, DNS safety is obligatory.
DNS safety as a part of a robust defense-in-depth technique
A cybersecurity technique that makes use of a multi-faceted method to safeguard an data know-how (IT) infrastructure is named a defense-in-depth technique – and DNS safety is and have to be thought to be certainly one of its key elements.
A defense-in-depth technique incorporates redundancy in case one system fails or turns into prone to assaults with the intention to defend towards a wide range of threats.
Relating to DNS safety, you should bear in mind each the endpoints and the community.
Endpoint DNS safety
Study extra about endpoint DNS safety, particularly DNS content material filtering and menace looking, beneath.
- DNS filtering: DNS content material filtering is the method by which an web filter restricts entry to a specific web site’s content material based mostly on its IP handle moderately than its area identify.
DNS content material filtering strategies embody class filters (for instance, racial hatred, pornography web sites, and so forth.), key phrase filters (limiting entry to particular web sites or internet functions based mostly on key phrases discovered within the content material of these web sites), and administrator-controlled blacklists and whitelists.
- Menace looking: Menace looking, one of many key elements of contemporary cybersecurity, is the method of figuring out and understanding menace actors who could compromise an organization’s infrastructure by concentrating on recurring behaviors.
Utilizing the presumption of compromise, menace looking is a proactive cyber protection tactic that lets you give attention to potential dangers in your community that will have gone undetected.
What must you do to make sure endpoint DNS safety?
Search for a safety resolution that features a threat-hunting part.
You’ll be able to seek for a safety resolution or suite with a threat-hunting part. With a view to enable you to block malicious domains, communications to and from command-and-control (C&C), and malicious servers, it ought to proactively consider site visitors and filter all community packages.
Community DNS safety
When it comes to community DNS safety, you should bear in mind the rise of BYOD and IoT and clearly set up how you establish who and what connects to your on-line community perimeter – particularly in mild of the shift towards distant or hybrid work that we have witnessed within the final couple of years.
Rise of BYoD
Carry your individual machine (BYOD) coverage refers back to the follow whereby staff join their private units to the networks of their employers and carry out on a regular basis duties.
Among the advantages of BYOD embody diminished prices, elevated worker productiveness, and better employees satisfaction, however the disadvantages are equally value mentioning: excessive (and even greater) safety dangers, potential lack of privateness, a scarcity of units, and the necessity for a extra advanced IT assist system.
Essentially the most important threats {that a} BYOD coverage implies are cross-contamination of information, a scarcity of administration and outsourced safety, unsecured use and machine an infection, safety breaches and GDPR considerations, obscure functions, hacking and focused assaults, phishing, adware, spy ware, exercise recording software program, insufficient insurance policies, and final however not least, human error and mixing enterprise with pleasure.
Rise of IoT
The bodily gadgets which can be embedded with software program, sensors, and different applied sciences that allow them to attach and alternate knowledge with different units and programs over the web are known as web of issues (IoT) objects.
A powerful variety of elements, reminiscent of easy connectivity and knowledge switch, entry to cheap and low-power sensor know-how, elevated cloud platform availability, developments in machine studying and analytics mixed with the large quantities of information saved within the cloud, and the rise of conversational AI, have all contributed to the emergence of IoT.
The dangers to IoT safety are substantial. Threats to identification and entry administration, potential knowledge breaches, the rising variety of units and the substantial assault floor, insecure consumer interfaces or the comfort of units, poor software program updates, and the benefit with which somebody with bodily entry to a product can extract the proprietor’s password from the plaintext, non-public keys, and root passwords are just some examples.
What must you do to make sure community DNS safety?
Search for an answer that may defend your organization on the perimeter/community degree.
By using community prevention, detection, and response know-how, robust community safety options successfully remove threats. They will work together with firewalls to forestall malicious requests from reaching perimeter servers within the first place.
Methods to reinforce DNS safety
Though a excessive share of companies acknowledge the significance of DNS safety, the typical time to mitigate assaults elevated by 29 minutes, now taking 6 hours and seven minutes, with 24% taking longer than 7 hours, based on the 2022 World DNS Menace Report.
The quantity of misplaced time interprets into misplaced income, so it is vital to concentrate on different methods for enhancing DNS safety to make sure you do not find yourself being the following sufferer of malicious gamers. Listed here are some examples:
Onsite DNS backup
You would possibly take into account internet hosting your individual specialised backup DNS server to enhance DNS safety. Though managed DNS service suppliers and Web service suppliers can each be attacked, having a backup is essential not simply within the occasion of a deliberate assault in your vendor. {Hardware} or community failures are extra steadily guilty for DNS efficiency issues or outages.
Response coverage zones
Using response coverage zones (RPZ) is an extra technique for enhancing DNS safety. A nameserver administrator can use RPZ to offer different responses to queries by superimposing customized knowledge on prime of the worldwide DNS.
How can a response coverage zone assist? Effectively, with an RPZ, you possibly can:
- Direct customers to a walled backyard with the intention to stop them from accessing a identified malicious hostname or area identify
- Forestall customers from accessing hostnames that time to subnets or identified malicious IP addresses
- Prohibit consumer entry to DNS knowledge managed by nameservers that solely host malicious domains
IPAM
Web protocol handle administration (IPAM) is a system that permits IP handle administration in a company setting. It does this by facilitating the group, monitoring, and modification of information pertaining to the IP addressing house.
The community providers that assign IP addresses to machines in a TCP/IP mannequin and resolve them are DNS and Dynamic Host Configuration Protocol (DHCP). These providers shall be related by IPAM, enabling every to be told of modifications within the different. For instance, DNS will replace itself in accordance with the IP handle chosen by a shopper through DHCP.
Safety duties automation
Automation is among the key methods for rising DNS safety and must be used each time and wherever potential.
Automated options can assist you reply to potential safety threats with superior menace intelligence, take care of security-related points routinely in actual time, and collect essential safety metrics, in addition to streamline breach incident response. Furthermore, it may decrease human enter in time-consuming remediation duties and enhance worker productiveness, but additionally velocity up breach incident response and support in making well-informed selections.
Conclusion
Regardless of being the muse of the web as we all know it, cybercriminals have typically chosen DNS as a goal with the intention to reap the benefits of vulnerabilities, entry networks, and steal knowledge.
What does this imply for companies? Lack of cash, time, model harm, in addition to potential fines and authorized repercussions.
Each enterprise should due to this fact pay attention to probably the most important safety dangers that DNS implies, together with DoS, DDoS, DNS hijacking, DNS spoofing, DNS tunneling, DNS amplification, DNS typosquating.
Equally essential is understanding what you are able to do to ensure DNS safety. Companies can select to make use of response coverage zones, onsite DNS backups, IPAM, DNS content material filtering, and IPAM. Most significantly, they need to attempt to automate safety duties and discover safety options that depend on superior menace looking elements.
Relating to staying forward of cyberthreats, prevention will all the time be the perfect plan of action.
Able to bump up your safety? Discover the perfect DNS safety software program to safe DNS servers and the web sites they assist.